We use the ‘Cohesive Way’ to build and deliver the VNS3 Network Platform. We are not unique, but our approach helps us be distinctive.
Latest Posts
Owning our mistakes, “mea culpa” from Cohesive’s CEO
Learning from our mistakes.
To agent or not agent, the CrowdStrike question
How do you decide if the risk of a security feature is worth it? If the cure can be as bad as the illness how do you decide? We have opinions!
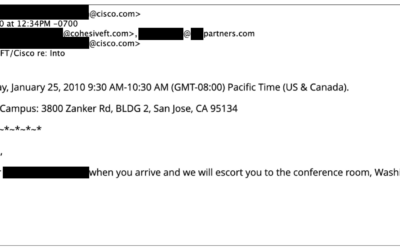
Cisco owes me a sandwich!
The folks at Futuriom put up a piece with suggestions for Cisco as it struggles with who it was and who it wants to be. In that vein here is an anecdote from the early days of Cohesive Networks.
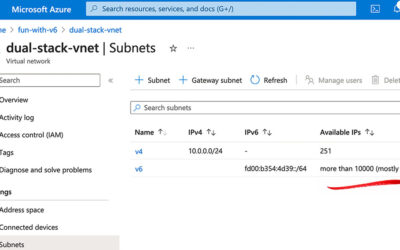
Migrating to IPv6 – Managing the Madness (Pt. 1)
As enterprises transition to IPv6, managing naming conventions becomes crucial. Devices require unique names for DNS and monitoring purposes. We’ll explore taxonomies for naming devices in production environments, including examples of technical, organizational, and asset management schemes. Stay tuned for Part 2: implementing IPv6 in your organization.
ZTNA: Is it really the end of VPNs?
While the Zero Trust Network Architecture (ZTNA) movement has been hailed as a game-changer for network security with many calling it the end of VPN. This blog post argues a combined approach that incorporates multiple security layers is key to securing the enterprise.
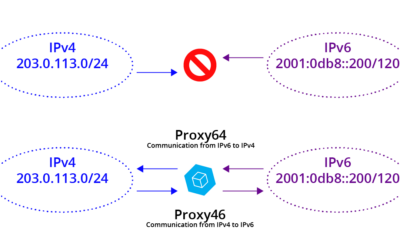
Moving to IPv6 – herein lies madness (Part 2)
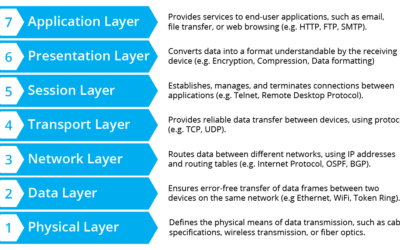
For the enterprise, IPv6 is upon us. Here is how your network and application administrators can adapt. The are two Internets now. The IPv6 Internet is not related to the IPv4 Internet as you have configured it inside, outside, or at the edge of your Enterprise. IPv6 is not the next version of the Internet protocol; it is the next Internet.
Moving to IPv6 – herein lies madness (Part 1)
In a twisted paraphrase from the movie “Jaws”, it looks like we are going to need a lot more boats. IPv6 is here for the enterprise cloud and multicloud. I am going to need a lot of virtual machines for my VPC’s eighteen quintillion addresses.
Stand Apart – but be Cohesive
IPv6, Secure and Private AI are both upon us, and Cohesive Networks is delivering into those areas with the same practical approach we have used for Public and Private Cloud all these years.
Navigating the Cloud Transition: Simplified Solutions for Legacy Applications
source:Dall-EOvercoming the Complexities of Cloud Migration with Cohesive Networks' VNS3 Plugin System Transitioning legacy applications to the cloud can be a daunting task. The challenges are...
Apple VisionPro – No security issues yet!
Cohesive VNS3 6.0 Beta3 is now available and free to use in AWS, Azure, and upon request. Get WireGuard(r) performance and encryption along with OIDC authentication, dynamic routing, global deployment capability, and integration to cloud and datacenter connectivity solutions today.
Enterprise WireGuard® with Cohesive VPN Client
Cohesive VNS3 6.0 Beta3 is now available and free to use in AWS, Azure, and upon request. Get WireGuard(r) performance and encryption along with OIDC authentication, dynamic routing, global deployment capability, and integration to cloud and datacenter connectivity solutions today.