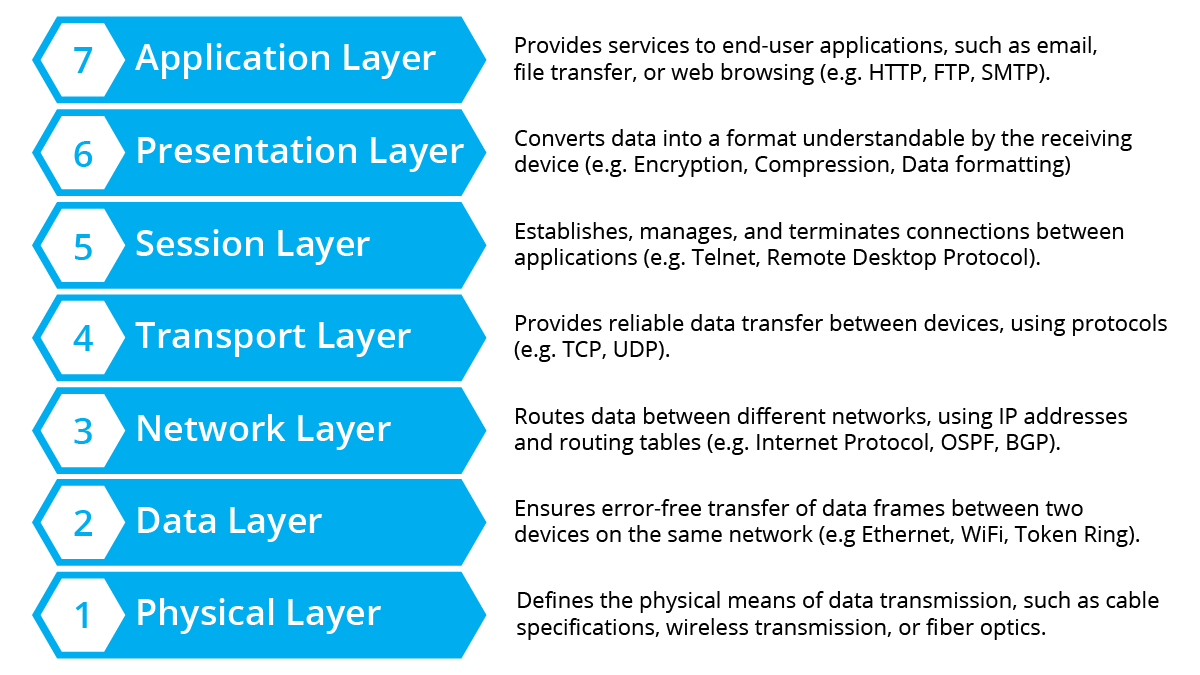
All of those devices running around your organization need a name, and in fact once we start naming things it won’t stop, we will have multiple names per device, because if one name is good, more are even better.
Of course organizations have been using DNS for years, and the Internet runs on it, but for B2B, enterprise, SaaS we have seen widely varying depths of use.
Some of our more advanced customers have adopted one or more taxonomies for naming devices in their production SaaS environments, albeit perhaps not throughout their internal organization. It can be somewhat of the cobbler’s children having no shoes, we do pay attention to our customers, but often not to ourselves. Here is an anonymized example of such a SaaS taxonomy:
<saas service name abbreviation>.<cloud>.<cloud account abbreviation>.<cloud region>.<production status flag>.<customer id>.<customer abbreviation>.<cost center id>.<machine id>.<cloud instance id>.domain
It is certainly a mouthful, and in fact more so than “fc55:636f:6865:7369:7665::6440:1fe3”, but since most humans DON’T do hex/decimal calculations in their heads, it works by providing understanding via the delineated labels in the full name.
Once you see this type of naming at work in administration and monitoring, you can then see why devices end up with multiple DNS names based on differing organizational taxonomies. We have see technical, organizational, asset management, project-based, and functional naming schemes for devices. At Cohesive we aren’t quite that complex, but if you ask Chatgippety or the LLM of your choice for examples they will provide some overly simplistic examples which give you the gist.
- dell.laptop.8gb.intel.corei5.lenovo.windows.10.ssd.departmentC.corporate.com
- marketing.sales.promotions.abrown.laptop.hr.central.branch.corp.com
- asset.laptop.s345678.la.abrown.decommissioned.finance.southern.us.corp.com
- project.gamma.phase3.teamC.abrown.task3.testing.chicago.corp.com
- function.sales.system.crm.module3.midwest.corp.com
Further Reading
If you have all of naming nailed, good on you. If you don’t here is a great overview by the folks at Cloudflare who create some great content for all of us: https://www.cloudflare.com/learning/dns/what-is-dns/.
For those who are more visual, here is excellent work from a redditor who seemed to have become inactive (sadly) three years back:
https://www.reddit.com/r/programming/comments/klaffg/dns_explained_visually_in_10_minutes/.
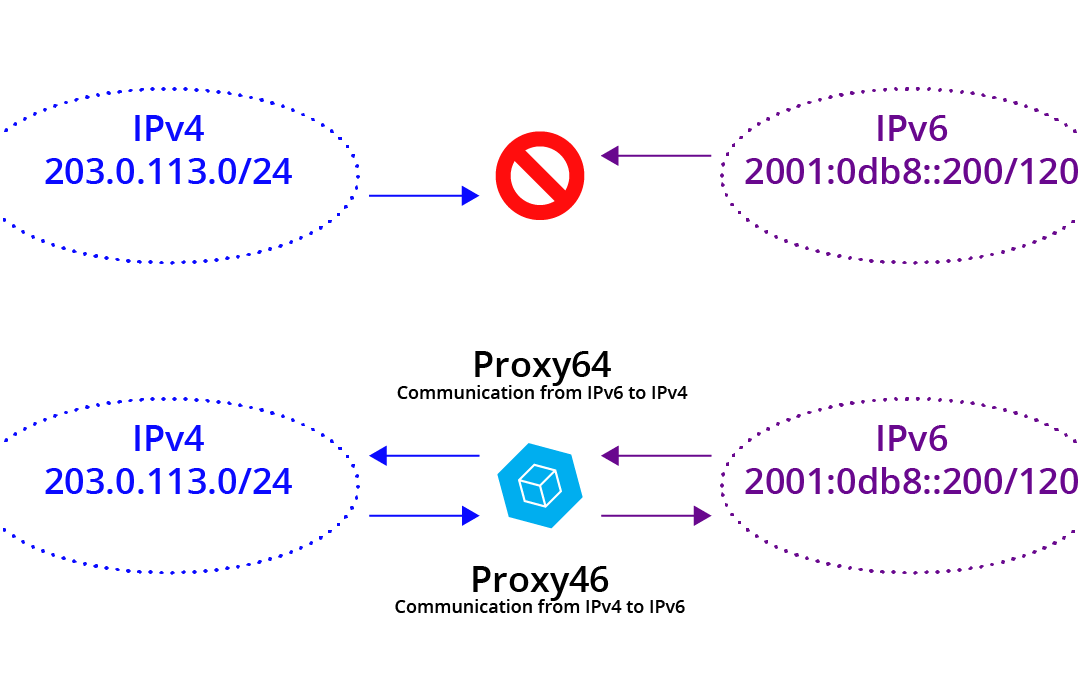
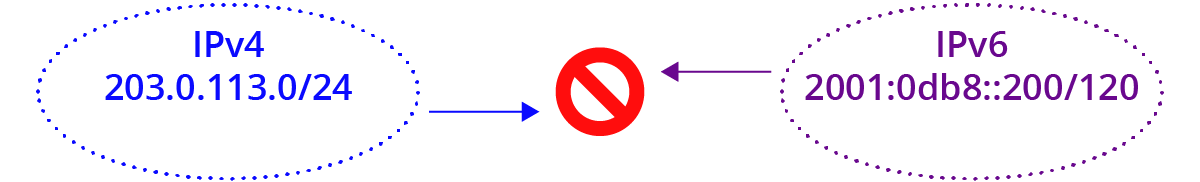
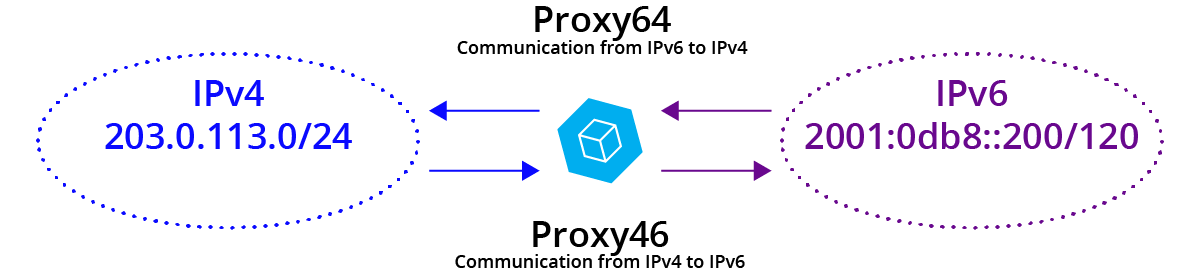
For more on the emerging challenges of the IPv6 world you can look back at a few Cohesive posts:
And if IPv6 addressing still has you perplexed the team at Oracle did a super job here:
https://docs.oracle.com/cd/E18752_01/html/816-4554/ipv6-overview-10.html.
AND – never forget the Rosetta Stone of IPv4 to IPv6 understanding here:
https://docs.google.com/spreadsheets/d/1pIth3KJH1RbQFJvZmZmpBGq6rMMBhqEmfK-ouSNszNY.
Next up we will show you how VNS3 version 6.6 for Internet6 will help you adopt IPv6 for cloud edge and cloud interior, provding network functions that are better, faster, cheaper than the competing offerings (to NAME just a few reasons to get a Cohesive network).







Recent Comments