How do you decide if the risk of a security feature is worth it? If the cure can be as bad as the illness how do you decide? We have opinions!

To agent or not agent, the CrowdStrike question
Some thoughts on the CrowdStrike events at a broad level. We don’t provide the type of capabilities they do, so I don’t feel comfortable inveighing on what happened and how it happened. But, we do have some thoughts on when to take the risk of deploying agents into your systems.
At Cohesive we have a standard response to customers wanting to install <fill in the blank agent> into our VNS3 Network and Security platform virtual appliances. It is always a difficult situation as it is being pushed by the security team and CISO, at what tends to be our larger, more revenue significant customers. It is difficult because our answer is a polite, yet vehement “no”.
The VNS3 control plane should only be open to an allow-listed operations ingress address. The data plane should be open to the ports and services you use our platform for. (We are often a cloud edge firewall, people vpn, data center vpn, waf, and more.) The biggest liability to the security and operational integrity of our devices would be to add an agent that can be exploited or can itself cause an outage. This has happened in the industry (but not to us) numerous times over the recent years via things like SolarWinds, Microsoft OMS agent, and now CrowdStrike to name a few.
One of the oft-used phrases at Cohesive is “horses for courses” and we use that British idiom as part of our approach to making architectural and deployment security recommendations. With respect to the panoply of agents that vendors and security teams alike argue to be installed in all your systems, we think it is quite apropos. We think you need to look at what the purpose and placement of the computing devices is in order to make this decision.

If it is a computer used by a person, especially hybrid use or remote use, how are are you going to protect it? For the most part you can’t protect the network it is on, since it is running on networks you don’t control.
There are some options outside of agenting, for example if using Windows operating system you could use group policy to force the machine onto a virtual network with no ability to access the Internet other than through your VPN’s edge, but it is bad user experience and expensive to have acceptable points of presence.
And even if forcing users onto a VPN, what about email phishing links and attachments, what about Microsoft Office macro exploits that leak into your shared drives? Super tough, and I am glad we aren’t in that business.
People make mistakes. Even well-trained, diligent people can make mistakes in where they browse to or what they click on, and you need to be able to address possible exploits there at the point of attack. So I can’t really blame someone for wanting to believe these types of products are the answer.
At Cohesive which admittedly is not a huge company, our answer has evolved from ‘Microsoft Office is disallowed’, to now ‘Windows is not allowed’. Right there the “people attack surface” is minimized. However, that is a long migration or a “never migration” for many companies. In these cases, I think “agent away” and be judicious in the vendor you choose.
What about business servers, the computers that are not the personal device of an end-user, but rather are there to perform a function like database or API serving or message queuing? Again, for Cohesive, easier in that Windows is not allowed, business services are built on Linux. That said, whether Windows or Linux, in these scenarios why are you ‘protecting’ the computer instead of the network? Those business servers are not going to click on links, browse bad websites, or download malware. They are automatons performing specific, repetitive operations.
This is where we are skeptical of the agent approach and will not allow it for our network appliances, and as applicable would not allow for business services. (CrowdStrike apparently created a similar issue previously on some Linux distributions: https://www.theregister.com/2024/07/21/crowdstrike_linux_crashes_restoration_tools)
In these cases the VNS3 Network Platform (or similar vendor offerings) is there to protect and monitor ingress and egress to the network, along with other elements of what should be thought of as a security lattice. Using cloud or data center virtualization, you have your cloud network security groups and network ACLs, along with your OS firewall, both of which should be working in tandem with network appliances like VNS3. You can then run WAF or IPS at these ingress/egress points as well – run them inside VNS3 or run them via an appropriate cloud service offering.
We think these are the rules to follow:
- Computer primarily used by human and it has to be Windows, agent it and anti-virus it.
- Computer primarily used by human and is Mac or Linux, anti-virus it.
- Computer used by computers, both micro-segment and protect the network, use a security lattice. The risk from any agents are too high.
- (OPTIONAL) Computers used by computers are ideally Linux servers using the distributions’ minimal install with at least some elements of CIS hardening.
But then you loudly proclaim, “we need visibility into the VNS3 (or other) appliances for our <DataDog, Syslog Server, SumoLogic, AlertLogic, etc..>!”
OK – you got us. We DO allow visibility to logs, network configuration and statistics, netflow, and some API calls for system status to plugins that run inside VNS3 – but don’t have full host access.
When you are running VNS3 controllers, whether a single one or a larger cluster, you are running a mini “docker cloud” inside your virtual network. We have a set of pre-built plugins as well as a published set of elements needed to make any open source, proprietary source, or commercial source that can be containerized, into a compliant plugin. This gives you the ability to put analysis and monitoring INTO the network, yet not be able to disrupt the network security device; observability with security.
(And now the sound of Cohesive patting itself on the back for this balanced approach to agenting.)
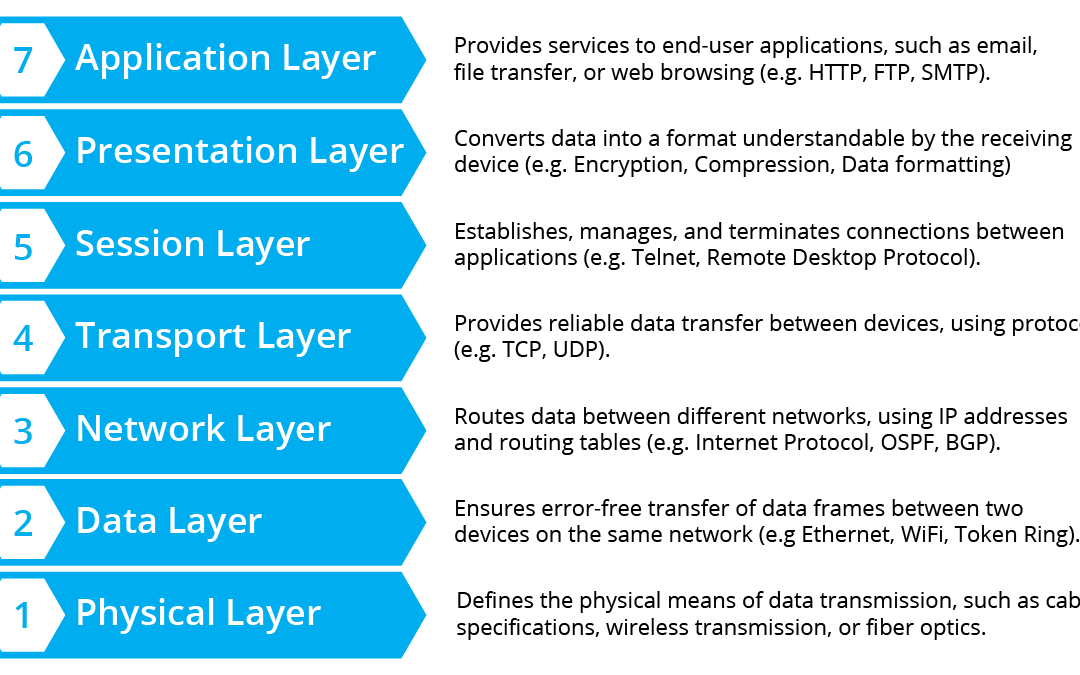
ZTNA: Is it really the end of VPNs?
The Zero Trust Network Architecture (ZTNA) movement has been around long enough that many vendors have proclaimed the “end of the VPN era” (1)(2)(3). While ZTNA offers valuable security benefits, we can’t help but wonder if this declaration is premature and naive.
Don’t get me wrong – ZTNA is a powerful approach to secure applications. By assuming all users are potential threats, it verifies, identities, and permissions before granting access to resources. However, relying solely on layer 7 (L7) solutions like those described by ZTNA advocates may leave your organization vulnerable to other types of attacks.
The Limitations of L7 Security
ZTNA’s focus on the application layer can’t address issues at the network layer. Few enterprises have HTTPS/web-based only infrastructure. It is more complicated than that at the network layer. This means that even with a robust ZTNA solution in place, you’re still exposed to threats like DNS spoofing, IP spoofing, and lateral movement.
Perhaps at the heart of our disagreement, if we had to pick “no vpns” vs. “everything is a vpn”, we would lean toward the latter. Your carrier network uses virtual private networks, your cloud subnets at AWS and Azure are virtual private networks, your VMware infrastructure running NSX is a virtual private network, and so it goes throughout the infrastructure used by well-secured enterprises. Oh and you’re technically reading this blog through a tunnel (encrypted communication channel established between your browser and the web server using TLS/SSL cryptography).
A Combined Approach is Key
Instead of relying solely on a simplistic definition of ZTNA, we recommend a combined approach that incorporates multiple security layers. This includes:
- Network segmentation: Divide your network into smaller segments based on business needs, reducing the attack surface and limiting lateral movement.
- Encryption: Encrypt sensitive data in transit using technologies like Wireguard, OpenVPN (SSL/TLS), and IPsec.
- ZTNA: Implement ZTNA to verify identities and permissions at the application layer.
- Network security appliances: Use network security appliances like firewalls, intrusion detection systems (IDS), and next-generation firewalls (NGFW) to detect and prevent threats at the network layer.
While ZTNA is an essential approach to a comprehensive network security strategy, it’s not a panacea for all network security issues. By combining multiple security layers, you can create a robust defense that addresses various threat vectors.
Don’t fall prey to the hype – take a balanced approach to securing your organization’s network.
The Enterprise and WireGuard
WireGuard® at its core is a lightweight, low code, VPN tunneling protocol that optimizes for speed, security and ease of configuration. However, extended business functions needed for enterprise usage are left out of its code base by design. This non-opinionated approach allows third parties to develop novel methods that best fit enterprise needs and styles.
Examples of Enterprise needs are:
- Key (re)generation and distribution for both human users and machine-to-machine networks
- RESTful API for integration to in-house systems and external services
- Uniform access to encrypted tunneling via regional or global clusters
- Dynamic routing so devices on the WireGuard network learn about network paths as they come and go
- Failover support allowing clients to migrate servers in the event of maintenance or outages
- Integration to security platforms (Firewalls, WAFs, IDS/IPS)
- Integration to other “tunneled” paths (IPsec, GRE, VXLAN, cloud direct connects, etc..)
- Integration to “legacy” monitoring tools like SNMP
- Integration to “modern” monitoring tools like Datadog and Sumologic
- Integration to legacy authentication (Active Directory)
- Integration to modern authentication (OAuth / OpenID, MFA, etc..)
- AND more!
Cohesive is working to make the WireGuard protocol a first order citizen in our VNS3 Network Platform with a focus on many of these extended capabilities.
Enterprises will need methods to securely store and distribute keys to human and machines. Authenticated REST APIs allow automation frameworks to tag and place keys where needed in a distributed computing environment. Self-service web portals give end users access to allocated keys for their various devices. Administrators and intrusion detection systems need the ability to revoke keys when compromise occurs.
Not all tunneling systems and their keys are the same. Many companies employ encrypted overlay networks, in cloud and between their compute nodes in order to satisfy regulatory requirements and gain network visibility. For automated machine-to-machine communications, public/private key pairs are all that is required, whereas with “people VPN” scenarios added authentication factors are needed.
In the dynamic world of cloud networking and remote work, private networks are now fluid, meaning that network address ranges are added and removed, as new networks and subnets come on line or are decommissioned. In order for systems to communicate they need dynamic route updates providing up-to-date paths through interconnected transit networks.
These encrypted tunneling systems are used to take the enterprise, its customer and partners to, through, and across clouds. This requires the WireGuard feature called “Allowed IPs” that acts as both ACL and route directives to be integrated. In Enterprise WireGuard use-cases, the “Allowed IPs” don’t come from a configuration file, they will be dynamically and seamlessly integrated to the broader systems routing and ACL policies. communications in the enterprise. Companies need the ability to filter and direct traffic at ingress and egress points in cloud networks.
WireGuard is fast becoming an essential operating system and developer tool, and Cohesive Networks believes it’s on its way to being an essential building block for creating robust, enterprise-ready network solutions.
“WireGuard” and the “WireGuard” logo are registered trademarks of Jason A. Donenfeld.

News Roundup: Week of Feb 21, 2022
U.S. Cyber Officials Issue Official Warning Against Potential Russian Cyber Attacks
During a call this Monday, FBI and DHS cyber officials urged government agencies “to look out for signs of Russian activity on their networks” as a result of the evolving Ukraine crisis. According to Yahoo: “federal officials also urged those on the call to dramatically lower their threshold for reporting suspicious activity.” Citing “an uptick in Russian scanning of U.S. law enforcement networks” as well as “in Russian disinformation and misinformation about Ukraine,” cyber officials urge increased care and caution with links and communications as the crisis progresses.
IBM Opens Cyber Security Hub in India
IBM recently announced the opening of their first IBM Security Command Center in the Asia Pacific region. The center hopes to provide a cybersecurity incident response plan for enterprise customers with deployments in the region, as well as “a fully immersive, interactive, and experiential learning facility.” IBM plans to use simulations and experiential training to help enterprises protect themselves from cyberattacks. IBM promises that by co-locating this training center with their X-Force Command Center, IBM’s Security Operations Center, both live practice and training for cyber security precautions will benefit immensely.
Microsoft Brings Cloud Security to GCP
Yesterday Microsoft announced the release of Microsoft Defender for Cloud for Google Cloud Platform, making Microsoft the first major cloud provider to offer security solutions in all major cloud platforms. The offering from Microsoft boasts Cloud Security Posture Management (CSPM) and Cloud Workload Protection (CWP) across both containers and servers. According to the release, GCP deployments of Microsoft Defender for Cloud will come “with out-of-box recommendations that allow you to configure GCP environments in line with key security standards like the Center for Internet Security (CIS).” Microsoft is also emphasizing the necessity of Zero Trust Management and event log management in cloud environments with two more ‘upgraded’ cloud security offerings.

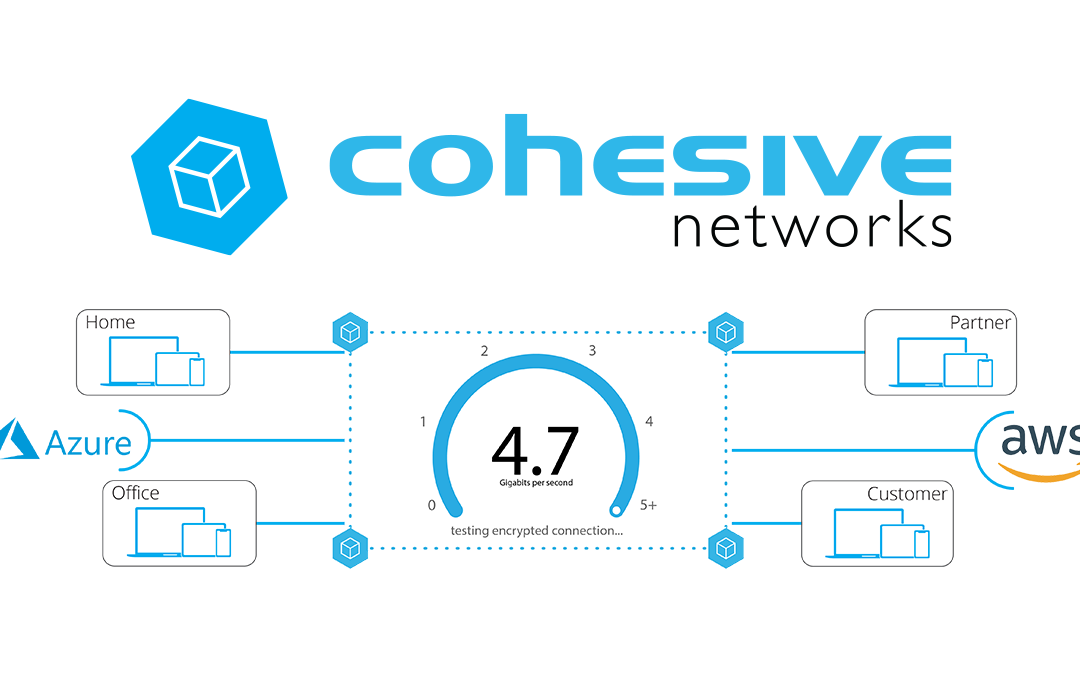
Distributed Hybrid MultiCloud Mesh with VNS3 and LNKe
As cloud adoption continues to ramp up in 2022, with Gartner projecting another 21.7% growth in cloud spend this year, companies are maturing beyond their initial workload migrations to single cloud vendors. Whether to create resiliency due to the now not so uncommon major outages we have seen in the past few years, to tailor their many application environments to changing business requirements, or to migrate to new cloud vendors whose offering is the best fit. However, in order to realize these opportunities, companies need a consistent network layer that is uncoupled from any one cloud vendors specific dependancies. No matter which cloud you choose, achieving this goal requires utilizing third party network solutions. Such a solution should ideally facilitate connectivity to data-centers, remote users, and IOT devices as well.

Cohesive Networks VNS3 cloud edge security controllers can create the backbone across all of your public cloud vendors in an easy to manage and secure mesh, with LNKe connecting all of your virtual private networks. This gives you a fully transitive network across all of your cloud real estate, running at performative speeds with built in failover and self healing mesh capabilities. Granular IPSec cloud edge configurations allow you to connect corporate data centers, partner networks and vendor access, regardless of their hardware. Policy enforcement is consistent across the network and has been simplified for ease of management. With our comprehensive firewall you can easily define people, groups and network objects to allow your remote workforce to securely connect at the edge closest to their physical location. In short, with VNS3 and LNKe, you can create a full network mesh consistent with your needs that can grow to anywhere that you need to be and scale with your deploments.
Please reach out to the Cohesive Networks sales and solutions team at contactme@www.cohesive.net to further the discussion with any interests that you may have. We are always happy to help.



Recent Comments